Grandstream’s GCC6000 Series redefines IT infrastructure with convergence devices that bridge the core technologies businesses rely on for their operations. IP PBX call handling, VPN routing for flexible/hybrid deployments, next-generation firewall security, and networking all come together in an all-in-one device. This blog post will provide a high-level overview of deploying a GCC series solution and its components. By reading this post, you will understand a GCC series device's features and functionalities and how to leverage them for your clients.

Looking for a complete technical breakdown? Visit our documentation center and access the GCC device's user manual.
GCC Overview
A single GCC device provides an immense amount of customization for small to medium deployments. Delivering a suite of technology that was once reserved for enterprise businesses with large budgets and IT teams, a GCC can easily and affordably be deployed to integrate into an IT infrastructure seamlessly. A GCC’s capabilities can be broken down into the following modules, which is how it is organized in this blog post:
- Networking
- Firewall
- Network Nodes
- IP PBX
A GCC convergence device can be accessed through its web browser GUI or Grandstream’s free, cloud-based management system, Grandstream Device Management System (GDMS). It is recommended to use GDMS for your Grandstream deployments as it comes with a suite of features to configure, manage, and troubleshoot your devices that are unavailable via the device’s GUI.
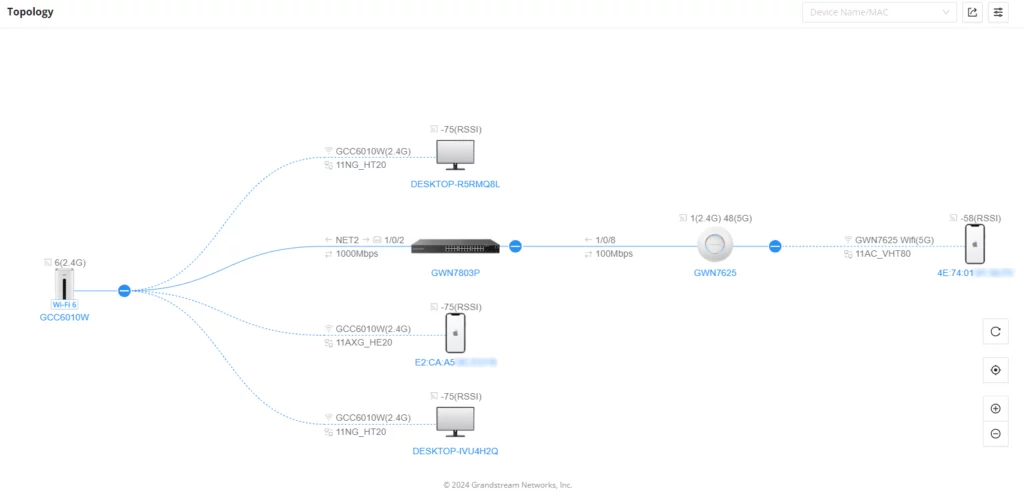
Before diving into each module, it is essential to understand some of the core system settings of the GCC series. First, a Topology setting is available that enables a system administrator to view a network map of all devices connected to a GCC. This is extremely helpful when managing additional devices within the network and during the GCC’s configuration process. Basic system settings such as system scheduling, user management, and email alerts should be set before setting up your device.
Networking Module
When setting up a GCC device, the Networking module is where an administrator can find vital IT infrastructure settings such as WAN/LAN configurations, VLAN creation, VPN management, routing policies, QoS features, and more. This module brings important network control features and deep data/traffic customization to a deployment. This section will highlight some of the largest features within the Networking Module and provide a brief overview of how to utilize them.
Network Settings
Within the network settings submenu, WAN, LAN, and port configuration options can be found. Through the port configuration menu, users can adjust the settings related to all the GCC device ports. This includes the Gigabit Ethernet ports and the device's SFP ports. This includes flow control, speed, duplex modes, and if the port is a LAN or WAN. Flow control can also be set here. Users will also be able to adjust the PoE capabilities of the ports, which are only available on PoE models. WAN port configuration can be done via the WAN submenu, which allows users to connect the ports to a DSL modem on our router and supports setting static IPv4/IPv6 addresses.
VLAN
The LAN configuration page contains many features for more complex network deployments. This is where VLAN creation can be found. Creating a VLAN provides a group of host devices with a standard set of requirements that allows them to communicate as if they were attached to the same broadcast domain, regardless of their physical location. A VLAN has the same attributes as a physical LAN but allows endpoints to be grouped and isolated even if they are not on the same physical network switch. Within the VLAN port settings configuration menu, a user can use LAN ports to allow only specific VLANs on each port. Together, these settings will enable the network to be properly segmented for both overall security and to pair with QoS features to help optimize network performance.
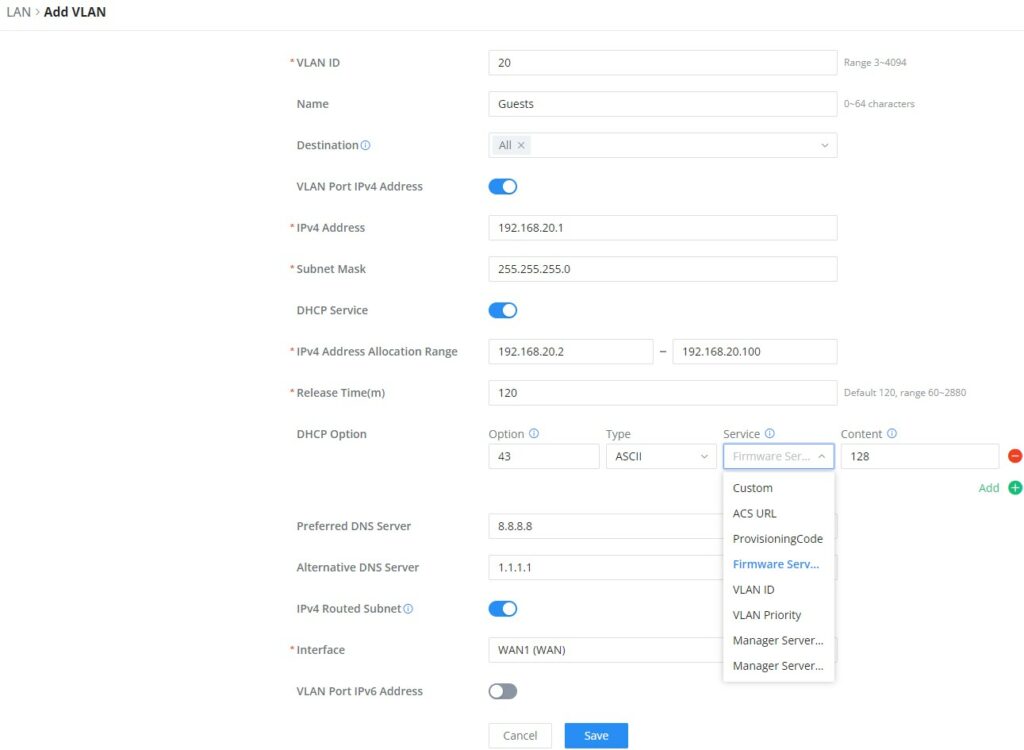
VPN
A critical feature for many deployments, Virtual Private Network (VPN) settings are used to create an encrypted connection, enabling users to exchange data across shared or public networks acting as clients connected to a private network. The available VPNs can be modified within their respective settings, which you can find more about here. The GCC series supports the following VPNs:
- PPTP: Client and server
- IPSec: Site-to-site and client-to-site
- OpenVPN®: Client and server
- L2TP: Client
- WireGuard®: Server
Policy Routes and Load Balance Pool
The user can create a policy route to either load balance or backup (Failover) between 2 or more WAN ports. This feature allows a network administrator to make advanced routing decisions for traffic passing through the router and for high granularity control over policies dictating WAN port and even VLAN traffic. Traffic controlled this way can be balanced across multiple VLANs. Static routing can also be adjusted within this menu item by manually configuring the routing entries rather than dynamic routing traffic.
Quality of Service (QoS)
QoS settings allow the prioritization of specified traffic between WAN and LAN hosts. This enables in-depth network customization and guarantees the performance of specified services with finite control over limited bandwidth usage. This is particularly useful in deployments that see large changes in bandwidth usage, such as in hotel deployments. General QoS settings allow for allocating a percentage of download and upload bandwidth between 4 classes that can be assigned to applications to determine which application traffic will be prioritized during periods of heavy network usage. Applications can have their classes assigned under the QoS’s APP Class submenu. Further class rules can be set based on source and/or destination IP addresses, as well as source and destination ports.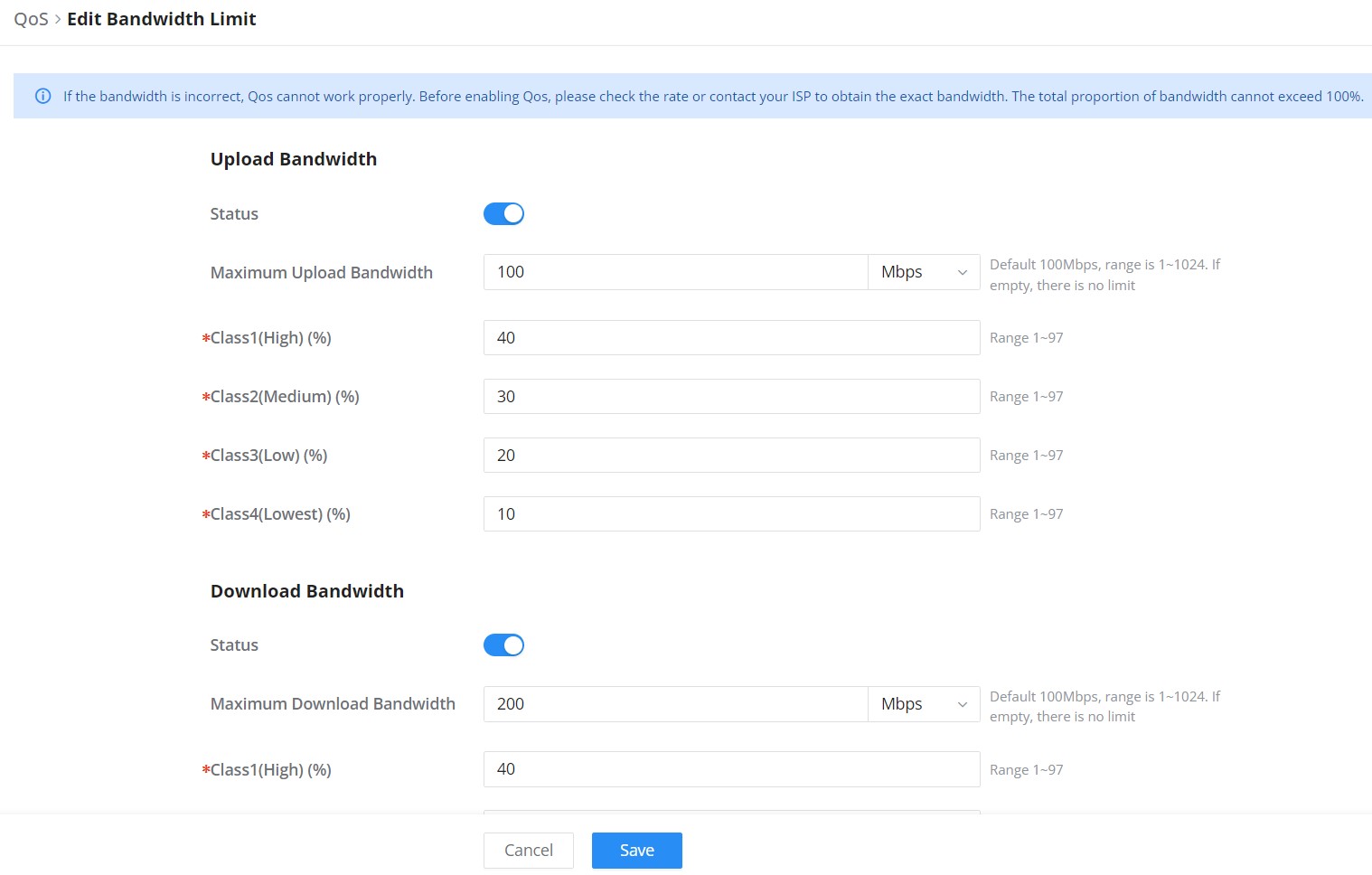
Bandwidth Limit
For finite bandwidth control, a specified maximum upload and download limit can be set and applied to specific IP/MAC addresses or a range of IP addresses. Once a new bandwidth rule is added, a user can choose the IP Address/MAC address to apply the bandwidth constraint. After this, a maximum upload and download can be set. Lastly, a schedule can also be selected to have the bandwidth limit running only during specific times.
Network Nodes
In network management, network nodes refer to individual devices or components, such as switches and access points, that form the interconnected infrastructure being monitored. These nodes provide data points for analysis, helping the monitoring platform assess the overall network's health, performance, and security. After accessing your GCC’s Network Nodes interface, the overview web page will provide an overall view of your GCC’s performance and network information. In this section, we’ll discuss the essential features to be familiar with within the Network Node module of the GCC.
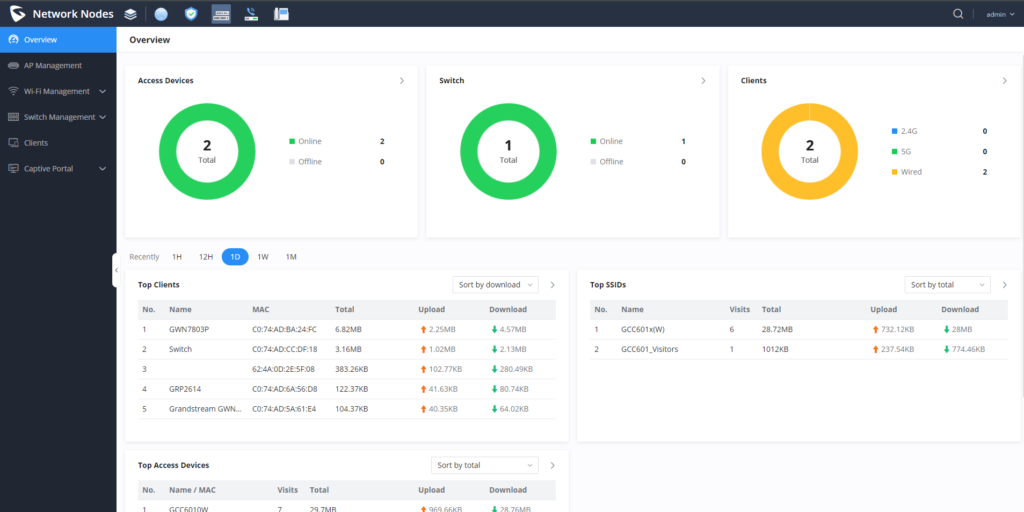
GWN Access Point Management
Grandstream’s GWN access point can be fully configured and managed within the Grandstream Device Management System, alternatively they can also be managed directly through the GCC with its embedded controller. This is helpful when a deployment requires devices to be configured and managed locally, allowing configurations to be pushed from the GCC’s AP controller to the GWN access points for centralized management. Management of GWN access points can be done in great depth. From the GCC, you can:
- Configure Access Points
- Upgrade Access Points
- Delete Access Points
- Reboot Access Points
- Transfer Access Points
- Assign SSIDs to Access Points
- Locate Access Points
For more information on the embedded GWN controller of the GCC series, click here.
Wi-Fi Management
Within this submenu of the Networking Nodes module, users can fully customize SSIDs, Private Pre-Shared Keys, Radios, Mesh settings, and Blocklists on the Wi-Fi network. When creating a new SSID, it can be associated with a VLAN within the GCC’s configurations. Additionally, access security can be set from here, and captive portals are associated with the SSID for client access. Advanced settings such as client inactivity timeout, schedule for the SSID to be available, wireless client limits, and more can be set for a fully tailor-made network. Essential Wi-Fi selections such as Band Steering, Airtime Fairness, channel width, radio power, and more can be found in the Radio settings. Lastly, Mesh settings can be found on the GCC within the Wi-Fi Management submenu. To configure GWN access points in a Mesh network successfully, the user must pair the access points first with the GCC, then configure the same SSID on the access points.
Switch Management
In the same way that GWN access points can be configured, managed, and monitored through the GCC’s onboard controller, GWN switches can be controlled via a GCC device. This includes configuring, monitoring, and optimizing switches for efficient resource allocation and network troubleshooting. The GCC series simplifies switch management, allowing organizations to adapt their network infrastructure dynamically without significant physical hardware changes, enhancing agility, and enabling on-demand service delivery. For a list of currently supported GWN switches and their firmware necessities, visit our page here.
Switch configuration can be done both individually and globally. Settings such as the VLAN ID that the switch will use, static or dynamic IPv4 address configuration, RADIUS authentication, and more can be set individually. The Global switch configurations will apply their parameters on the GWN devices within the network. This includes detailed RADIUS options, the VLAN for IGMP snooping and MLD snooping, jumbo frame size, and more. Lastly, the Port Profile submenu options enable users to apply many settings to a GWN switch port simultaneously for quick batch setting changes and adjustments. Speeds, native VLANs, duplex mode, flow control, port isolation, storm control, security settings, and more can be adjusted in bulk. Once the Port profile/settings are created, the user can apply it on a GWN device/device group port.
Client Customization and Management
Within the Network Nodes module, the Clients page lists all the devices and users connected currently or previously to different LAN subnets with details such as the MAC Address, the IP Address, the duration time, the upload and download information, etc. Client devices can not only be monitored here but also have access to the network adjusted and optimized from this page. This includes setting a maximum upload and download bandwidth, a schedule for these limitations, VLAN for the devices, and having its static IP set.
Captive Portal
The Captive Portal feature on GCC601x helps define a Landing Page (Web page) displayed on Wi-Fi clients’ browsers when attempting to access the Internet. Once connected, Wi-Fi clients will be forced to view and interact with that landing page before Internet access is granted. Captive portals provide a robust set of customization options that can be leveraged to provide a refined experience for any wireless deployment. More information on Captive Portal creation can be found here.
Firewall
GCC devices have comprehensive firewall capabilities that can be leveraged to protect networks from external and internal threats. From DoS defenses to advanced content control and application filtering, this module's features revolve around maintaining a secure IT infrastructure.
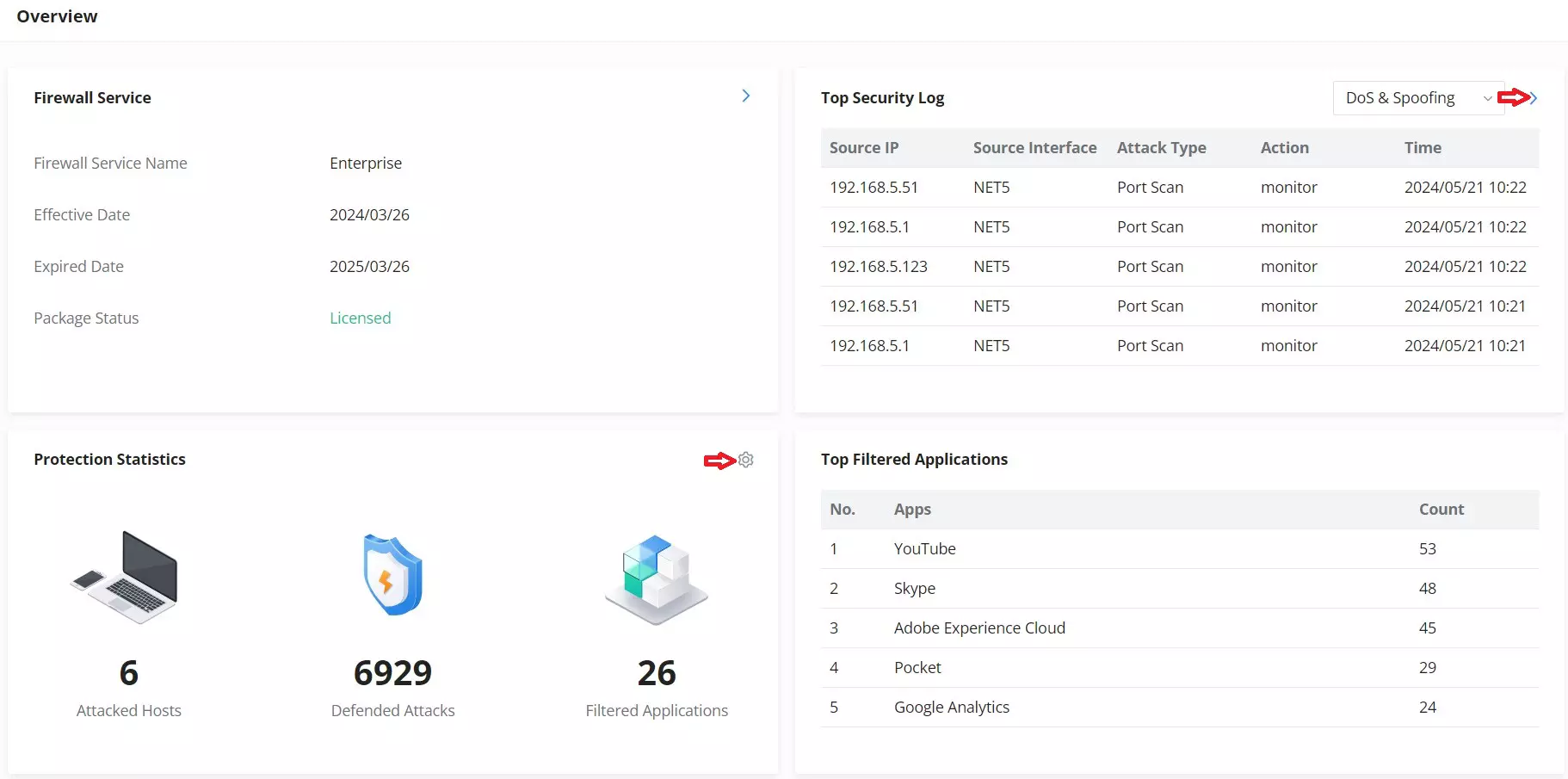
Firewall Policy
Data policies and rules can impact the GCC's handling of inbound traffic. Inbound rules can be configured to filter traffic to network groups or WAN ports and apply settings such as accepting that traffic, denying it, and dropping the packets. Forwarding rules allow the GCC device to allow traffic between different WAN/VLAN/VPN groups and interfaces, allowing the network to forward traffic from a specified source group to another. Lastly, advanced Network Address Translation (NAT) allows SNAT and DNAT mapping of private or internal addresses to public IP addresses or vice versa.
Security Defense and Anti-Malware
Within these two submenus in the Firewall module, DoS defense can be set and customized. UDP, ICMP, and ACK flood attack defenses can be toggled along with various abnormal packet attack defenses. Thresholds can also be set with these defenses, allowing for a greater level of customization for when the attack defense triggers and begins blocking packets. The spoofing defense section offers several countermeasures to the various spoofing techniques, such as blocking ARP replies with inconsistent source MAC addresses. Once the anti-malware is activated, a data packet depth can be set. The deeper the depth, the higher the detection rate and CPU consumption. There are three levels of depth: low, medium, and high. Users can check scanned files and virus detection statistics on the overview page. Through the virus signature library, users can manually update their anti-malware library or adjust how often it is updated (by default, this occurs randomly between 00:00 and 06:00 every day.)
Intrusion Prevention
Intrusion Prevention System (IPS) and Intrusion Detection System (IDS) are security mechanisms that monitor network traffic for suspicious activities and unauthorized access attempts. IDS identifies potential security threats by analyzing network packets and logs, while IPS actively prevents these threats by blocking or mitigating malicious traffic in real-time. IPS and IDS provide a layered approach to network security, helping protect against cyberattacks and safeguard sensitive information. A botnet is a network of compromised computers infected with malware and controlled by a malicious actor, typically used to carry out large-scale cyberattacks or illicit activities.
Content Control
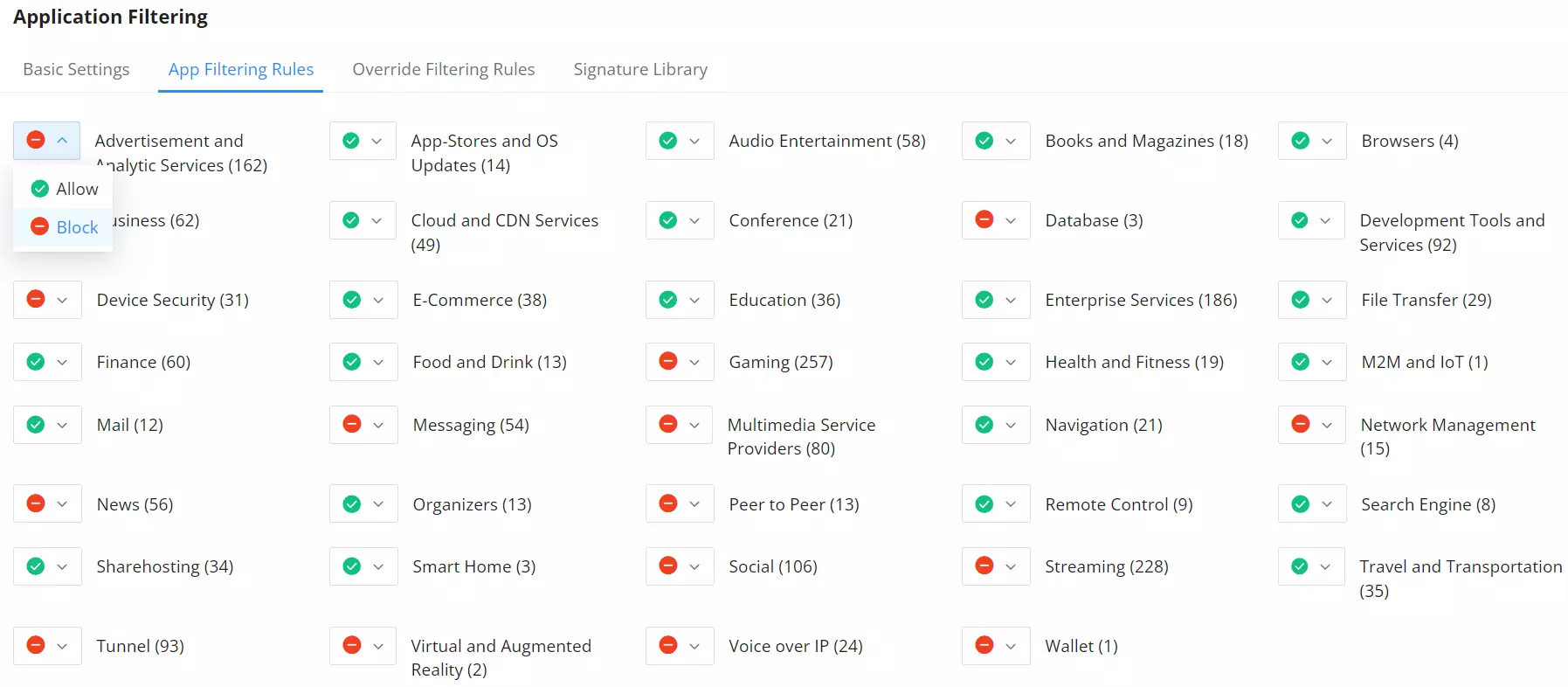
Using filters based on DNS, URL, keywords, and applications, the content control setting can create a finite set of rules that will block traffic user traffic, preventing internal users from accessing potentially dangerous or malicious sites and applications. Within these settings, web filtering can be defined to avoid specific URLs or entire categories of websites. Keyword filtering can also be leveraged to prevent any website from utilizing that keyword from being accessed. Application filtering can be used to prevent access from entire sets of web services and websites. This could be auxiliary peer-to-peer services, file transfer applications, or social websites.
IP PBX
Finally, the IP PBX module is where the user can configure and manage the GCC series devices' call handling and collaboration features. This includes extension/trunk configuration, extension groups, outbound and inbound routes, Interactive Voice Response (IVR), voice mail, call center capabilities, ring groups, paging/intercom features, and more. If you are familiar with our UCM series of IP PBXs, the GCC has almost all of the same features and customizations available. The IP PBX features are so robust that it is too much to go into within this blog post. If you’d like to learn more about it, you can visit our documentation page here.
Additionally, Grandstream offers a one-time expansion package and add-ons for the IP PBX module of the GCC6000 series to increase its maximum number of users and concurrent calls. For more information, visit our plans page here.
More on the GCC Series of Convergence Devices
The GCC6000 series offers a complete IT infrastructure solution for small to medium businesses and deployment verticals that can’t be found anywhere else. We created the GCC Demo Tool so you can browse through the GCC’s features and capabilities. You can access the visually interactive demo environment by clicking here and typing “Admin” for the username and password.

Are you ready to take the next step and begin deploying GCC Series Convergence solutions for your clients? Through our Contact Us page, you can contact our sales team and connect to a distributor for your area.

























.webp?width=250&height=131&name=how-to-use-gdms-q1-2024%20(1).webp)
















