When discussing a UC solution with a customer, security is likely a top concern of theirs. In recent years, it seems as if the more information we put over the Internet, the more vulnerable we become. However, trying to explain cryptographic protocols to someone without a VoIP background can get a bit dicey, and it’s easy to get lost in a sea of acronyms. For today’s blog, let’s discuss a brief overview of VoIP communication and encryption at an accessible level.
Overview of VoIP Communication
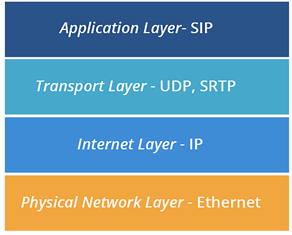
Before we get in-depth, let’s first go over a simple explanation of how VoIP communication works. When information is sent over the internet it gets sent as tiny packets, comprised of various layers, each layer plays a role in moving the process along, kind of like an assembly line. The layers work to make sure that your information arrives in the right order so that it makes sense. For the sake of this post, we will focus on the Application layer and the Transport layer as illustrated in the diagram below. If you are using a VoIP phone then the application is SIP. In this case, SIP signals the call to begin. Next, the transport protocol tells the call’s voice information how fast it should go and in what order it should arrive in. To read more about transport protocols for voice, see my previous blog post here.
What is SRTP?
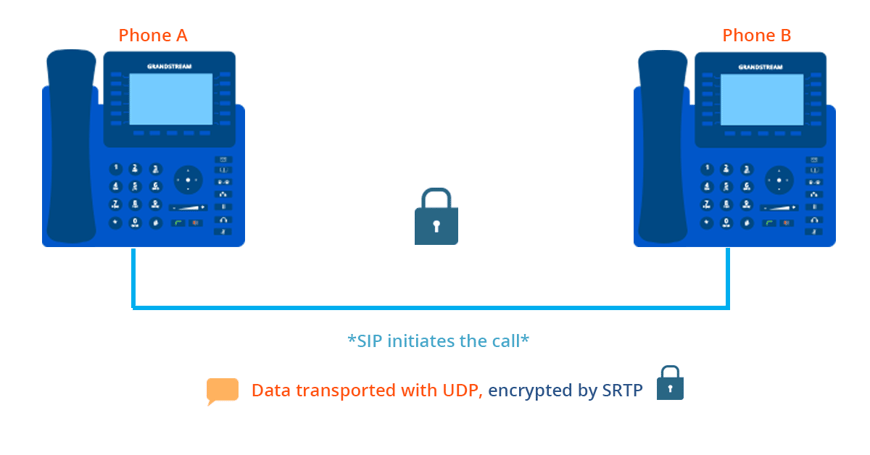
When data is being transmitted through VoIP it requires a transport protocol. Secure Real-time Transport Protocol (SRTP) provides encryption, message authentication, and replay attack protection to the voice data being sent, making it ideal for VoIP. Although it has transport in the name, it is simply a cryptographic protocol meaning that it performs the function of applying algorithms that encrypt and protect your information as it is transmitted. Think about SRTP like the seatbelt in a car, it has no impact on the route the car travels, or how fast it goes but it protects the contents of the car on its journey.
SRTP is desirable because it uses the Advanced Encryption Standard (AES) to protect the VoIP media. AES is the same standard used by the US government, financial institutions, and other organizations internationally to protect and secure their information.
If you want to make a truly encrypted call, SRTP must be enabled by both parties on a call. On a Grandstream phone, to indicate that the encryption is active for both parties a lock icon will appear near the extension number. This way, before the call goes through, the caller knows their information is safe.
What about SIP over Transport Layer Security (TLS)?
TLS works to encrypt different information than SRTP. When using TLS, call data like phone numbers and user names won’t be decipherable. It also prevents eavesdropping and message tampering. So, while TLS and SRTP are both cryptographic protocols, they protect different types of information.
SRTP can be complex, but hopefully this blog post helped to introduce you to the basics of SRTP and VoIP encryption. Learning about the many features Unified Communications offers, especially when it comes to security, is imperative when we use the Internet to transmit voice data daily.
Want to learn more about Grandstream’s UC offerings and various software integrations? Download our guide here.